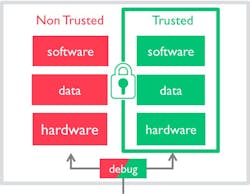
You may not be aware of ARM’s TrustZone technology or what it does, but chances are you interact with it every day when you access your smartphone or tablet computer. As described by ARM, TrustZone is “hardware-based security built into system on chips (SoCs)…to provide secure end points and roots of trust.” ARM explains that its TrustZone recognition of secure (trusted) and non-secure (non-trusted) worlds extends beyond the CPU, its memory and software to include transactions on a bus, interrupts and peripheral functions within an SoC.
Essentially what we’re talking about here is embedded hardware levels of security that extend beyond IT methods of security, such as firewalls, DMZs and whitelisting, to more securely protect a device from cyber intrusions. Bedrock Automation, for example, employs an ARM-based secure microcontroller as part of its proprietary Black Fabric Cybershield technology—an embedded deep trust cyber defense using patented processor, memory, communications, interconnections, backplane and packaging technologies to integrate cybersecurity into the company's industrial control system modules. The use of such secure, embedded technologies is finding increasing use in automation systems of all kinds.
At the Embedded World event in Nuremberg, Germany, February 23-25, I spoke with two companies targeting industrial automation about their use of embedded ARM security.
At the Mentor Graphics booth, I spoke with Warren Kurisu, director of product management at Mentor Graphics and Alan Grau, president of Icon Labs—which supplies embedded networking and security technologies for Mentor Graphics products. At the booth, Kurisu highlighted Mentor Graphics’s IoT (Internet of Things) Gateway SysDK (system design kit). This customizable IoT gateway is designed to help industrial companies link legacy infrastructure and devices to the Internet for IoT applications.
This gateway, Kurisu explained, allows for customization of the gateway’s software while using embedded hardware to maintain security. Key to the gateway’s ability to allow this is “ARM TrustZone technology—the hardware secure environment used on smart phones,” Kurisu said. “With this technology installed on the gateway, you can access devices connected to the gateway to update all of them within the protection of the ARM TrustZone installed on the gateway.”
Historically, industrial security has followed the IT strategy of secure pipes, access control and firewalls, but it is now moving to “hardware-based security proven on consumer side,” Kurisu said. “Silicon Valley thinking is being integrated into industrial systems.”
Icon Labs’s software is used to validate operations on the gateway in the ARM TrustZone. This means that there is “no interference with run-time operations,” Kurisu added, noting that Mentor Graphics’s Nucleus RTOS is also safety certified via IEC 61058 SIL 3.
“The value in this [capability] is that it allows software emulation of security without having to change existing hardware in device,” Grau noted.
Read more here about Mentor Graphics and Icon Labs work to secure industrial devices by design.
Telit is another company relying on embedded ARM technology, among other embedded hardware security technologies, to secure its industrial networking products. The company’s deviceWise product for integrating plant-floor automation systems with the enterprise is well-known in the industrial space (read how Honda integrated its production and enterprise systems using deviceWise).
The deviceWise product is a key element in Telit’s approach to IoT, which John Keever, CTO of Telit IoT Platforms, explains as being "focused on IoT as a means to an end to improve business.”
Leveraging deviceWise, Telit’s IoT Portal—a cloud-based IoT service for factories— is designed to enable bi-directional communication between intelligent IT and OT assets. As described by Telit, the company’s IoT Portal service lets companies configure and manage end-to-end IoT deployments from a single, cloud-based portal to “connect things to apps” by integrating any device or production asset with web-based and mobile apps and enterprise systems, across any wireless network.
A lot of companies provide gateways to connect devices and systems and communicate data. “With deviceWise, we have the software that can also do analysis functions at the edge device level, such as handling the pre-processing of collected data before sending it off to the cloud or another server for analysis," said Keever. "You can also embed deviceWise directly into a controller because it speaks the native protocols. It's a horizontal platform that can be used to solve vertical industry issues. With deviceWise, you can build a machine and ship it anywhere in the world and it can function there.”
With this approach, “we’re connecting plant floor devices to enterprise systems from the chip level,” Keever noted, underscoring the growing trend across the industry to look beyond the historical use of software applications as the means of integration.
The technology and application directions outlined here for Mentor Graphics/Icon Labs and Telit illustrate why you’ll be hearing more and more about embedded hardware security, such as ARM’s TrustZone, as you investigate the critical underlying technologies to enable industrial systems for IoT applications.
Leaders relevant to this article: