Industrial control system (ICS) security has been a major topic for more than a decade now. Over the past few years, the focus on ICS cybersecurity has become so predominant that numerous companies have been launched to address it.
Concurrent with this growth of the ICS cybersecurity market has been the growth in interest in the Industrial Internet of Things (IIoT). One could say that the two topics—ICS cybersecurity and IIoT—are inextricably linked, since the IIoT concept revolves around the connection of ICS devices via the Internet.
But while the focus on ICS cybersecurity has centered on in-plant devices and systems, the mobile devices used to connect to these devices via the IIoT h not received nearly as much attention. Though it could be argued that securing your plant and the devices in it will address any issues created by mobile device connections, considering the constantly moving target that is effective cybersecurity, it’s clear that any thorough IIoT cybersecurity action plan should also address the mobile devices used to connect to your ICSs.
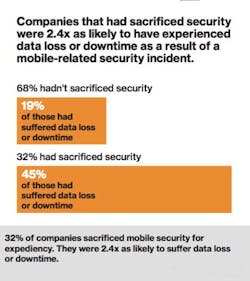
According to a recent study by Verizon, it appears that many companies don't yet have their enterprise, ICS and mobile device cybersecurity plans in synch. The study shows almost a third (32 percent) admitted to having sacrificed mobile security to improve expediency and/or business performance and more than a quarter (27 percent) said that, during the past year, their company had experienced a security incident resulting in data loss or system downtime where mobile devices played a key role. Forty percent of those who reported having an incident said that it had been major with “lasting repercussions.”
Some of the principal reasons, noted in the study, for the high incidence of mobile security breaches include the facts that: only 39 percent of companies change all default passwords on their mobile devices; only 38 percent use strong/two-factor authentication on their mobile devices; less than half (49 percent) have a policy regarding the use of public Wi-Fi, while even fewer (47 percent) encrypt the transmission of sensitive data across open, public networks; and only 59 percent restrict which apps employees download from the Internet to their mobile devices.
One particularly interesting finding of the Verizon study is that a lack of budget for mobile device security is not a contributing factor to the mobile device cybersecurity gap. In fact, 52 percent of respondents said that their mobile device budgets have increased in the past 12 months, while just 2 percent said it decreased. The problem causing the lag in mobile device security is apparently lack of user awareness. Twenty-three percent of respondents said that lack of awareness among device users was a significant barrier to mobile security, with only 12 percent saying their device users “know a lot about mobile security.”
The Verizon study was, of course, a cross-industry effort—meaning that multiple types of industries were included, such as financial services and healthcare. In terms of study specifics related to manufacturing, the report indicates that “cyberespionage was the predominant motivation for breaches in this [the manufacturing] sector.” While outside attackers and cyberespionage are of statistical concern to the manufacturing industries, however, Verizon points out that costly downtime from malware that doesn't even specifically target manufacturers may cause the most damage. The report states that, while the number of manufacturing companies that had experienced an incident was low compared to other sectors, it was still nearly one in five (19 percent). And over three quarters of manufacturing respondents (79 percent) agreed that mobile devices pose a risk.
To help manufacturers address their mobile device security concerns, the Verizon study points to five aspects of 4G LTE mobile device security that should be considered by all companies relying on mobile device access to their systems:
- Secure storage. With 4G LTE, a Universal Integrated Circuit Card (UICC) token holds credentials and secure data for accessing services provided by the mobile network. The private key is created when the UICC is manufactured, and is only shared with the carrier in a secure way, preventing this data from being intercepted and used for illegitimate purposes. Personal Identification Number (PIN) and PIN Unblocking Key (PUK) mechanisms are enforced on the UICC to secure access to data or applications on the LTE network. This provides cryptographic primitives and secure storage of key material that cannot be corrupted by the surrounding hardware and software on the handset. The UICC itself is a tamper-resistant compute platform and supports multiple cryptographic algorithms.
- Airlink encryption. When 2G was the prevailing standard, it was possible to intercept mobile phone calls as they passed over the radio waves. From 3G onwards, encryption of data transmissions has made this much more difficult. LTE encrypts both data and signaling to prevent it being overheard on the radio access interface. Most LTE networks support 128-bit encryption.
- Mutual authentication. In LTE networks, the network authenticates the user identity, while the user equipment authenticates the network credentials. Mutual authentication protects against attacks from rogue base stations, thereby defeating any kind of man-in-the-middle attack. The UICC contains the necessary authentication algorithms and certificates, which aids in the secure accessing of the network. During initial attachment to the network, a temporary mobile subscriber identity is used instead of the international mobile subscriber identity to protect the subscriber from being identified.
- Integrity protection. Signaling is the means by which the network and the user’s handset exchange messages to verify identity and control calls. This has been exploited in earlier mobile standards to spoof identity and intercept calls and data. Integrity protection is used to verify that the signaling has not been modified over the radio access interface, and that the origin of signaling data is the one claimed. Each signaling message is appended with an integrity tag and the message is accepted only upon verification of the integrity by the receiving end.
- Stronger encryption. The use of 128-bit keys in 4G LTE doubles the key strength compared to previous standards.