What is the #1 concern about vertical integration in industrial automation? You guessed it: security. And even in the context of OT (operations technology) networks in industrial automation, it makes sense to work with your IT department because these folks have a lot to offer. They have experience with security and integrating security into networks, and we can draw from this experience as we integrate IT and OT networks.
But we need to have an understanding on priorities, because in the IT world, confidentiality is paramount followed by integrity and availability. In the OT world, these priorities are flipped. In OT, availability is paramount because we need to ensure controllers can perform real-time data exchange to keep the factory operating. Then we are concerned with integrity and finally confidentiality.
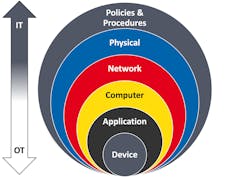
Defense in Depth
Even if there is disagreement with this shift in priorities, the one thing we can all agree on, no matter what side of the aisle you are on, is the concept of Defense in Depth. This is a concept where we look at the network holistically and build layers of security—like the layers of an onion—so if a malicious actor gets through one layer, there is another layer to provide the next level of protection. And then another layer, and another layer and so on.
For those unfamiliar with DMZs, these prevent direct data access. Data must first be put in a neutral location and then it can be retrieved by the other side. There also are industrial firewalls and DMZs available today that are intended for OT networks, meaning they are ruggedized, have a graphical user interface and provide simplified administration tools that can be used by control engineers. As we move down into computer, application, and device security, we find security tailored more toward OT networks where availability is the priority. And this is where Profinet comes in.
Netload test
Up until now, our current approach at PI has been to recommend a Defense-in-Depth strategy and, on top of that, we require that every device passing through the test lab for certification to undergo a so called “netload test.” This is where we subject the device to a flood of network traffic to simulate a denial-of-service attack and make sure that the device not only degrades gracefully but recovers automatically.
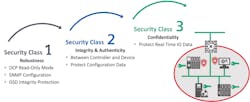
Security classes
- Class 1 is where we tighten up security for the DCP and SNMP protocols, and we protect GSD files.
- Class 2 is where we use authentication between a controller and a device to ensure a device is allowed to be on the network. This helps prevent man-in-the-middle attacks.
- Class 3 is where we encrypt the real-time I/O data, which is helpful if the data contain sensitive information like recipes, formulas or other trade secrets.
These scalable security classes, starting with Class 1, will become available in the next year or so, with Classes 2 and 3 following. If you are interested in additional details regarding security and PI’s security classes starting with Security Class 1, please visit the Profinet Security Guideline at https://www.profibus.com/download/profinet-security-guideline and , of course, contact us any time here at PI North America.
Tom Weingartner is technical marketing director at PI North America.