Cyber attacks across the manufacturing and critical infrastructure sectors have clearly become more prominent and concerning over the past few years. Through much of the reporting done on this topic, we’ve learned two things: 1) attacks from nation states have clearly been detected and 2) the increasing connectedness of plant floor devices and systems, which provide the pathways for attackers to access industry, is giving rise to a new set of technology suppliers developing products specifically designed to protect manufacturers.
Since the Industrial Internet of Things (IIoT) and the connectedness of manufacturing technologies is clearly key to industry’s future, it’s important to better understand both the methods and types of attacks used to access manufacturing systems. The 2018 Black Hat Edition of the Attacker Behavior Industry Report from Vectra, a provider of cyber attack detection and threat hunting technologies based on artificial intelligence (AI), provides some key insights.
The report uses data gathered by Vectra based on its monitoring of network traffic and collected metadata from more than 4 million devices and workloads from its customer cloud, data center and enterprise environments.
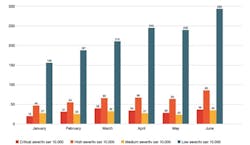
Looking specifically at data gathered from manufacturing sites in this report, the monthly volume of attacker detections per 10,000 host devices shows a higher volume of malicious internal behaviors compared with other attack types. Whether internal or external, malicious behaviors noted in this report fall into five method categories: botnets, command and control, internal reconnaissance, lateral movement and exfiltration.
Data breach methods
Following is a brief explanation of each of the five data breach methods mentioned above:
- Botnets tend to be a more opportunistic method of attack that leverages multiple computers located in a variety of sites to carry out an attack, typically a distributed denial of service (DDOS) attack. The Vectra report notes that the occurrence of botnet use in manufacturing is not particularly significant and is most often associated with user desktops that browse the web.
- Command and control is a growing threat vector for manufacturing as remote access technologies are adopted. According to the Vector report, “IIoT devices can be used as a beachhead to launch a [command-and-control] attack. Once an attacker establishes a foothold in IIoT devices, it is difficult for network security systems to identify the backdoor compromise.”
- Internal reconnaissance. Based on its monitoring, Vectra notes that there has been a spike in internal reconnaissance behaviors in manufacturing due to internal darknet scans and server message block (SMB) account scans. Internal darknet scans occur when internal host devices search for internal IP addresses that do not exist on the network. An SMB account scan occurs when a host rapidly makes use of multiple accounts via the SMB protocol, which can be used for file sharing, remote procedure calls (RPC) and other lateral movement. Vector notes that internal reconnaissance is often used to map a manufacturing network in search of critical assets to steal or damage.
- Lateral movement is the name for an attack method that describes what happens when connected systems and devices communicate with each other across a network—authentication and SMB brute-force behaviors are the most common applications of this method. The Vectra report describes SMB brute-force behavior as when an internal host uses the SMB protocol to make multiple login attempts for the same user account, which most often fail. During the monitoring conducted for this report, Vectra observed a high volume of automated replication, which indicates an internal host device is sending similar payloads to several internal targets. According to the report, in many instances, there is a 2:1 ratio of malicious behaviors for lateral movement vs, command and control.
- Exfiltration involves the export of data to an outside site. Vectra notes that data smuggling is the most prevalent form of exfiltration in the manufacturing industry. According to the report, “With data smuggling, an internal host device controlled by an outside attacker acquires a large amount of data from one or more internal servers and then sends a large data payload to an external system.”
Hacker motivations
Within the Vectra report, information from the 2018 Verizon Data Breach Industry Report is included to highlight the potential intent and motives behind cyberattacks in the manufacturing industry. That report says that state-affiliated attackers account for 53 percent of breaches in manufacturing. In these breaches, the most common types of data stolen were personal (32 percent), company secrets (30 percent) and credentials (24 percent).
Judging from the high rates of data theft related to personal data and company secrets, it’s not surprising that the Verizon report notes cyber espionage as a major motive behind the cyberattacks in manufacturing. Forty-seven percent of all attacks in manufacturing were conducted to gather this type of data, according to the report. Not surprisingly, financial motives (often played out with ransomware) took the No. 1 spot, with 53 percent of attempted attacks against the manufacturing industry being driven by this factor.
Underscoring the serious intent of the hackers targeting manufacturing sites, the Verizon report points out that 58 percent of breaches in manufacturing compromised at least one server. According to Verizon, the more general, opportunistic breaches in manufacturing usually focus on endpoints and IoT devices. However, attackers who plan to steal intellectual property and/or map out critical assets tend to target servers.
Reflecting on the findings of its own monitoring, coupled with the Verizon data, Vectra points to the “higher-than-normal rate of malicious internal reconnaissance behaviors” in manufacturing as an indication that attackers are “mapping out manufacturing networks in search of critical assets to steal or damage. And the abnormally high level of lateral movement behaviors is a strong indicator that attacks are proliferating inside the network.”
So, if your business is still somewhat on the sidelines when it comes to cybersecurity because you think that manufacturers are not such a big target for hackers, it’s time to reevaluate your thought processes. Manufacturers of all sizes and types are being targeted for a variety of reasons.
Take the time to speak with your trusted vendors or system integrators to find out what more you can do to protect your operations.
Sponsored Recommendations
Leaders relevant to this article: