Cybersecurity is on every manufacturer’s mind these days as more machines are connected and more groups and alliances emerge as a way to promote security standards and best practices for automation applications. While the focus has been on the control systems as a result of some high profile data breaches, there are probably a thousand other “little things” on the network—from sensors to 3D printers—that could potentially be an open door to a bad actor.
With that in mind, Deloitte, which partnered with Dragos in 2017 to expand its cyber risk services for industrial control systems, recently polled over 4,200 professionals to gauge how much they understand the risk exposure of Internet of Things (IoT) devices. Based on the feedback from the respondents, there is still a lot to overcome when it comes to IoT and cybersecurity.
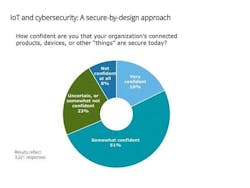
When asked: How confident are you that your organization’s connected products, devices, or other “things” are secure today?, the consensus was, “not very.” More than half of the respondents (51%) were somewhat confident, while 23% were uncertain or somewhat not confident. Only 18% said they felt very confident in their organizations’ ability to secure connected products and devices.That left 8% who stated they are “not confident at all.”
According to Deloitte, this lack of confidence may be the result of an overall lack of standardization across industries for security and awareness of cyber risks and connected devices.
Meanwhile, the number of cyberattacks, data breaches and overall business disruption caused by unsecured IoT devices are increasing because companies don’t know the depth and breadth of the risk exposures they face.
According to Deloitte Risk & Financial Advisory’s cyber practice and Dragos, the top 10 security risks associated with the current IoT environment include:
1. Not having a security and privacy program
2. Lack of ownership/governance to drive security and privacy
3. Security not being incorporated into the design of products and ecosystems
4. Insufficient security awareness and training for engineers and architects
5. Lack of IoT/IIoT and product security and privacy resources
6. Insufficient monitoring of devices and systems to detect security events
7. Lack of post-market/implementation security and privacy risk management
8. Lack of visibility of products or not having a full product inventory
9. Identifying and treating risks of fielded and legacy products
10. Inexperienced/immature incident response processes
“Security needs to become embedded into the DNA of operational programs to enable organizations to have great products and have peace of mind,” said Sean Peasley, an IoT security leader in Cyber Risk Services at Deloitte. “Today all sorts of products are becoming a part of cyber: from ovens to instant cookers, 3D printers to cars. Organizations need to consider what can actually go wrong with what is really out there and look at those challenges as a priority.”
To “embed” security into IoT, Deloitte and Dragos suggest a security-by-design approach, including ongoing monitoring and assessment of threats, to manage the risk of industrial control systems (ICS) and operational technology (OT) environments. Once the threats to the environment are understood, companies can develop cybersecurity strategies.
Of course, Deloitte and Dragos are offering a service to help. The collaboration combines the Dragos asset inventory and ICS assessments platform to map networked assets and provide continuous monitoring, which the Deloitte Secure Operations Center offers as a managed service. The secure-by-design aspect of this includes incorporating cybersecurity practices into the environment. That includes: understanding the current state of the product security; adding risk assessments, threat modeling and security testing into the design of the network architecture; engaging the right people to have ownership of the process, from leadership to security subject matter experts; and leveraging industry-available resources.
To that end, a positive revelation in the Deloitte poll results showed that 41% of respondents look to industry and professional organizations for guidance in driving security-by-design within their companies. Another 28% said that they look first to regulatory bodies and agencies that set the standards; and 22% indicated their leading practices were developed internally for providing that guidance in driving security-by-design.