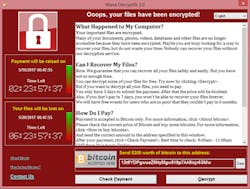
Possibly the biggest cybersecurity news item to come across the wires since Stuxnet was last week’s news about WannaCry. WannaCry is a type of malware referred to as ransomware because it blocks access to the infected computer’s data until a ransom is paid to regain access. It began infecting Windows-based computers worldwide on May 12 through phishing emails and a self-propagating worm feature in the malware.
Later that same day, a researcher at MalwareTech helped slow the advance of WannaCry by exploiting a kill switch in WannaCry’s code, which involved registering a web domain obtained from a sample of the WannaCry code. Doing this had the effect of sinkholing the malware’s traffic generated to spread its code. Though this kill switch might capture Internet traffic generated by the malware, it does not stop the malware from propagating its code.
Patrick McBride, chief marketing officer at Claroty, noted that because “many ICS [industrial control system] networks are closed off from the public Internet, the kill switch may not trip if the malware initially launches inside a closed network. The irony is that organizations that follow the best practice of having closed ICS/OT networks may remain at risk. In addition, some organizations inadvertently fueled the spread of the virus in their networks by blacklisting the kill switch URL.”
Though the first news items about WannaCry highlighted its impact on the British National Health Service, it affected more than 230,000 computers in 150 countries. Among the sites affected by the malware are the production operations of Nissan, PetroChina and Renault.
Because WannaCry was not specifically designed to target operations technology (OT) networks, it could be easy for manufacturers to dismiss it, said Galina Antova, co-founder of Claroty. “But…we have first-hand knowledge that the worm impacted OT networks and shut down production,” she said.
Although agreeing that malware like WannaCry is a threat to OT networks, Eddie Habibi, CEO of PAS, stressed that WannaCry should not cause manufacturers to panic. “This is one case where proprietary systems have an inherent defense mechanism against a widespread cyberattack like WannaCry,” he said. “Proprietary layers of OT that include Level 0 through Level 2 are generally immune to malware like WannaCry. The reason for this is that WannaCry is a Microsoft Windows vulnerability that, by design, cannot execute on traditional proprietary layers of the OT. This is important for the public as well as the authorities to know in order to not create unnecessary panic.”
Despite this Level 0-2 immunity, increasing links between IT and OT systems across industry hold the potential to dramatically impact industrial operations. McBride noted several key weaknesses that ICSs have in the face of malware like WannaCry, such as:
- Industrial networks are often not well segmented between IT/OT, so an infection in the former can easily spread to the latter.
- Microsoft Server Message Block is present within ICS environments that rely on Windows machines supporting HMIs, engineering workstations, historians, distributed control systems and more. WannaCry malware exploited a vulnerability present in Microsoft Server Message Block.
- Many Windows machines inside ICS environments are not fully patched and are often either outdated or unsupported.
Though the worst of the initial WannaCry seems to have passed, experts warn that a new version—without a kill switch—might already be circulating.
“Regardless of whether there is a new version in the wild, we expect copycat variants soon,” McBride said. “It is trivial to create a variant. All the required code is open sourced and the Conficker worm, which went through multiple transformation and infection cycles, serves as a good reminder” of this possibility.
Weak Spots
Though WannaCry may not be a huge cause for alarm for OT networks, it is a threat that can and has affected manufacturing operations worldwide. Therefore, manufacturers should be aware of the specific vulnerabilities they need to address to protect their networks.
Though the “hard real-time control systems, such as PLCs and embedded DCS controllers, have not moved to a Microsoft environment, almost all other parts of process control systems have moved to Microsoft Windows servers, MS SQL databases and Windows desktop operating systems," noted Barak Perelman, CEO of Indegy. "These parts of the control system can be vulnerable to the threat with different levels of impact on the processes they control.”
Those other parts of the control system include HMIs, engineering workstations, historians, tag servers, statistical process control (SPC), and laboratory information management (LIM) systems, said Bryan Singer, director of industrial cybersecurity services and sales at IOActive. In other words, “pretty much the entire body of knowledge to operate the OT environment and all the associated regulatory data is at risk,” he stressed.
Thomas Nuth, director of product and solution marketing at Nozomi Networks, pointed out that supervisory control and data acquisition (SCADA) and manufacturing execution systems (MES) are the points of highest vulnerability on any OT network becuase of their proximity to conventional IT functions and Internet access. “The average SCADA or MES often lacks the capability to actively monitor the industrial network for anomalous activity, making the identification of cyber threats in real time almost impossible," he said. "Furthermore, as SCADA and MES become more advanced and connected to the cloud, they become more vulnerable to innovative cyberattacks. While maintaining firmware and software updates is important, operators may fail to do so on time and every time. This means that SCADA and MES serve as a gateway for OT attacks, and therefore should be a top focus of any manufacturer’s industrial cybersecurity strategy.”
Are You Protected?
In the aftermath of this attack, and facing the certainty that more attacks like it are on the way, manufacturers of all sizes need to address the vulnerabilities in their OT systems.
The first step is to conduct a rapid inventory of all Microsoft machines in your network, Nuth said. “Quickly identify all computers that have access to your Layer 1 and Layer 2 networks and patch them with the most recent patch available from Microsoft,” he said, adding that specific patches are available for legacy operating systems that date back to Windows Server 2003.
Without a complete and accurate inventory of Microsoft machines on your network, “it becomes a guessing game,” Habibi explained. “The problem is that most companies do not have easy access to this data—particularly across an entire enterprise. One of the methods we see used most often is an email sent to each facility asking whether they have systems affected by a published vulnerability. This means that companies are relying upon manual spreadsheets or the memory of their OT subject matter expert to do the vulnerability audit.”
The right approach, according to Habibi, is to have “an automated, evergreen inventory of systems within the facility—not just for workstations and other IT-based systems—but for programmable logic controllers, distributed control systems, smart field instruments and more. With a comprehensive view of cyber assets, vulnerability identification is a simple, accurate query. This works for vulnerabilities such as the one used by WannaCry, as well as ones found in Levels 0 and 1 within the process control network.”
A patch from Microsoft addressing the vulnerability exploited by WannaCry was released a month ago, Antova noted. However, “it often takes vendors time to certify that the patches will work and not break other things,” she said, adding that they should work very fast to do this and get certified patches out to their customers. “Even then, many customers will have to either wait for a maintenance window or make a risk decision to stop production and apply the patch.”
As a further precaution, Singer suggested that manufacturers should not allow mobile devices such as USB, 4G data modems, untested laptops and field equipment to be connected to their OT networks. “Also, check firewall configurations to ensure Windows SMB ports, SNMP and pretty much anything on an OT network does not have any sort of external access from the Internet,” he said. “This includes VPN tunnels.”
Applying the Patch
Since a patch addressing WannaCry is available, McBride recommended the following six-step process for manufacturers:
1. Apply the Windows SMB Patch as soon as possible. An emergency patch for unsupported versions of Windows, such as Windows XP, Vista, Server 2003 or 2008, is available for older systems as well. (See Microsoft Security Bulletin MS17-010 – Critical).
2. Block SMB ports (139 and 445) between IT/OT networks.
3. On systems that don’t require use of SMB, disable it altogether (Microsoft instructions can be found here) or block it using the endpoint firewalls.
4. On systems that might require SMB for services that are less important, consider disabling SMB 1 until patches can be applied.
5. Quickly review disaster recovery plans and determine which Windows-based ICSs have current back ups. Image or backup those systems as soon as possible to aid in rapid recovery if these systems become infected.
6. ICS security teams need to remain vigilant for new variants of the WannaCry.
“Once systems that can be patched have been updated, organizations should take a hard look at those systems that can’t be patched and consider other ways to protect them,” Perelman said. “They should also keep in mind that vulnerable systems, such as PLCs and embedded DCS controllers, which aren’t Windows-based, should also be protected. “
The upside to the WannaCry event for manufacturers is that it should serve as a wake-up call. Though most critical manufacturing systems were not affected—allowing manufacturing, in general, to dodge a bullet—the networks these critical systems are connected to are highly vulnerable if care is not taken to practice good cybersecurity hygiene.
“For Level 3 devices, the worst case scenario [of WannaCry] is that the historian or an advanced application server has to go offline for the duration of the patch upgrade,” Habibi said. “The good news is that the proprietary devices in charge of control and safety are designed to continue to operate even when the Windows devices are offline. Many of our customers are patching their Windows devices outside planned maintenance to deal with WannaCry.”
In addition to patching, companies should “verify the reliability of existing security controls, identify the potential for new ones via risk assessment, alert personnel to risk, refresh cybersecurity training and ensure backups are performing properly in case there is a need to recover quickly," Habibi recommended. "Finally, if it does not exist, companies should develop a crisis management plan that anticipates certain attack scenarios. Waiting for a compromised system and a production down situation is the wrong time to think through decision considerations and communication requirements.”
Planning Ahead
Regardless of how quickly and successfully industry addresses the WannaCry vulnerability, cybersecurity remains a moving target. There will always be new threats on the horizon.
To stay as much ahead of the curve as possible, Singer recommended that companies follow industry-leading guidance from sources such as ISA/IEC 62443, NIST Cybersecurity Framework, SANS Top 20 Critical Controls and others. “If you have not conducted a cyber vulnerability assessment or penetration test for your network, schedule one,” he said.
Defense in depth is the best approach for protecting any company, Perelman said, adding that this requires multiple layers of security addressing everything from perimeter and network defenses and including every critical asset in the plant. “The problem in OT environments is that, for decades, organizations haven’t deployed defense layers beyond the perimeter,” he said. “We can no longer ignore the fact that threats can find a way into these networks and that critical assets like PLCs, RTUs and DCSs must be protected.”
Nuth adds that “with the advancement and introduction of things like Cloud SCADA and multi-site MES, it is no longer feasible to assume that industrial networks can remain separate and insulated from the Internet.”
This means that manufacturers must adapt their approach to cybersecurity. Historically, manufacturers have taken a “top-down approach that has attempted to industrialize IT approaches to cybersecurity,” Nuth said. “The problem with this approach is that firewalls, while beneficial, only go so far. Manufacturers need to invest in an ICS cybersecurity strategy that is engineered for their environment first. In other words, a bottom-up solution to cybersecurity is required to scale from the industrial node level to Level 3 firewalls. Manufacturers need to invest in new innovations within ICS cybersecurity that offer a comprehensive approach, from asset management and vulnerability assessment, to real-time monitoring and anomaly detection.”
WannaCry Resources