Remote Access Grows Even as Cybersecurity Fears Surge
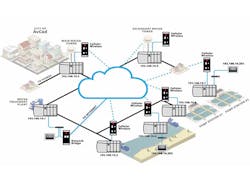
Remote access has been one of the more widely adopted Industry 4.0 technologies. In a recent survey conducted by Automation World, 67% of respondents indicated they are currently using some form of remote access to view machine and operations data. This high level of deployment is not very surprising when you consider that remote access is a key technology behind production monitoring, predictive maintenance, and aggregation of manufacturing intelligence across multiple sites. By granting end-users the ability to extract and aggregate data from numerous facilities, remote access can aid in optimizing production, reducing downtime, and coordinating enterprise-wide activities.
However, many in industry remain reticent about remote access due to concerns regarding cybersecurity and intellectual property theft. Even among companies who have adopted remote access, the systems being deployed and the applications for which they are used vary in scope and sophistication.
First, it’s useful to identify which industry sectors have been most receptive to the use of remote access technologies, as well as those that have been more resistant.
According to Travis Cox, co-director of sales engineering at Inductive Automation, oil and gas companies leaned into the technology much earlier than others due to the geographically dispersed nature of their assets and the fact that they already had satellite and cellular networks in use for similar applications, making deployment of modern remote access technologies easier to accept. With facilities and equipment being spread across such large areas, the reduction in travel that can be achieved via remote production monitoring is greater in oil and gas, for example, than in fields where assets are concentrated in a single location.
Similar trends are also visible in other continuous process industries. Cox cited wastewater treatment as an area where remote access has also been popular. In both industries, eliminating downtime is an important driver. Unlike discrete or even batch manufacturing, continuous process operations are just that—continuous. In the case of oil and gas, a small amount of downtime can result in large revenue losses. In a critical industry such as wastewater treatment, it could result in issues with the local water supply. As such, the ability to engage in real-time, continuous monitoring of equipment health for the purposes of preventative and predictive maintenance is vital.
The preference for remote access by companies with multiple production sites was further borne out in our survey. Among respondents with multiple production sites, 70% indicated they were currently using remote access technologies, while only 59% of those with single production sites were.
“The real reason there is more remote access among companies with multiple sites is that they’re trying to keep a handle on what’s happening across all the different systems so they can get an overall picture,” says Vishal Prakash, strategic product manager at ProSoft. “For someone with one site, they’re more likely to just give someone a call to get a picture of what’s happening; but for a plant manager who’s in charge of 10 different sites, every time he needs to get an update, he’s got to make 10 different calls. With some kind of remote access, he can get that information more quickly and easily.”
Yet remote access is also gaining steam in the discrete and batch manufacturing industries as well as among companies with a single production site. While companies with multiple production sites surveyed were more than twice as likely to have been using remote access for more than five years, plans for future implementations were more common among single-site operations. According to the survey, 70% of respondents whose companies operate a single production site plan to adopt remote access within one to two years, whereas only 50% of respondent companies with multiple production sites have similar plans.
Regarding discrete and batch manufacturing use of remote access tech, growth has been particularly strong in the past year, says Prakash. This is largely a result of COVID-19, which led many companies to turn to more remote technology to keep production moving apace with fewer workers onsite. Not only that, but many original equipment manufacturers (OEMs) and machine builders are integrating remote access into their products so that they can gather information about how their products are used to improve future designs or offer performance-based costing.
Still, despite growing enthusiasm for the technology, remote access cannot yet be considered ubiquitous across industry based on some key concerns. According to José Favilla, global Industry 4.0 leader at IBM, any industry segment, such as automotive, where intellectual property could serve as a substantial competitive differentiator, tends to be highly averse to remote access adoption. Moreover, while overall adoption has been strong among critical utilities such as wastewater and power generation, many holdouts still exist in these sectors due to concerns over cybersecurity. In these instances, if critical operations were to be disrupted or stopped, the consequences could be more dire than mere revenue losses.
How remote access is being used
On the uses remote access technology is being put to, our survey found that 45% of respondents reported using it for production monitoring, 63% for maintenance, repair, diagnostics, and troubleshooting, and 26% for gathering manufacturing intelligence for use by plant management or corporate executives.
According to Ranbir Saini, senior director of product management for automation products at GE Digital, these results are not surprising. Typically, production monitoring and maintenance-related diagnostics are the most fundamental applications to which remote access technologies are put, and are often the purpose for which they are adopted in the first place.
However, the use of remote access to aggregate manufacturing intelligence is a newer phenomenon that many companies have not yet managed to fully leverage the power of, Saini says. This process entails the collection and analysis of data pertaining to equipment health, material availability, and other metrics across numerous facilities to ferret out opportunities for enterprise-wide optimization. This kind of analysis tends to take place in the cloud, and may help C-suite executives more efficiently coordinate supply chain activity or otherwise identify waste they didn’t even know was occurring.
Growth in this kind of advanced analytics is bolstered not only by its increasing necessity in the wake of recent economic uncertainty, but by the fact that remote access capabilities installed by operations technology (OT) personnel for monitoring or maintenance purposes can serve as the infrastructure necessary for enterprise planners to build upon with more sophisticated digital transformation initiatives. As such, the growing prevalence of OT-oriented remote access projects aimed at improving field-level operations may have a ripple effect that accelerates the use of more sophisticated Industry 4.0 technologies.
"There are tremendous competitive pressures on companies today. This is a journey and remote access is step one. In order to get access to the data and aggregate that data to be able to analyze it or optimize it, you need some sort of remote access in place, especially if you're multi-site," Saini says. "Eventually, companies have to do this or they're not going to be competitive in the marketplace anymore.”
By far, the most prominent concern holding some companies back from adopting or expanding their remote access capabilities is cybersecurity. When asked what the biggest reasons for not permitting remote access at their facilities were, 85% of survey respondents cited fears related to cybersecurity. In fact, according to Favilla, that figure is too optimistic. “I’d say even more. Ninety percent or more are very, very worried,” he says.
Uneasiness has only grown in recent times as cybersecurity attacks have begun to take more diverse forms. For instance, the surge in ransomware—software that blocks access to a system until a fee is paid—has led some industries that have long been comfortable with remote access to begin reconsidering whether or not it is safe. As an example, Favilla mentions commodity industries, such as pulp and paper or textile manufacturing. Previously, companies in these fields were very open to using remote access, as they are not considered critical infrastructure and typically do not possess valuable intellectual property. Because of this, they did not see themselves as targets; i.e., hackers had nothing to gain by attacking their operations. However, through the use of ransomware, anyone can be shaken down or extorted for raw financial gain.
Fortunately, security frameworks have emerged to help companies navigate these challenges. Whereas companies once relied on perimeter strategies that used firewalls and other network-based strategies to inspect and validate users entering and leaving the network, this approach has become increasingly untenable as digital transformation has mandated that plants connect more and more devices outside of the information technology (IT) team’s control. As a result, defense-in-depth strategies that seek to use intentional redundancies at every layer of a system—down to the device level—helps ensure that proper security measures are becoming more common. These technologies require individual machines on the plant-floor to possess security certificates and only send data via encrypted communications.
In addition, IBM employs a “zero trust” model. This approach assumes that every connection and endpoint may be a threat, therefore it logs and inspects all corporate network traffic and employs stringent authentication measures. According to Favilla, the use of this model will become increasingly necessary at nearly all companies.
Favilla also mentions that ensuring security relies not only on deployable technologies, but on employee training and education. With many hackers gaining initial access to systems via phishing, the role human error could play in even the most sophisticated system cannot be discounted.
When it comes to solving the cybersecurity dilemma, the greatest challenge will be maintaining the availability and cost-cutting benefits remote access allows for while also improving safety through more restrictive security measures—a potentially tricky balancing act.
“We have to be continually verifying everything all the time, but it has to be in a manner that it does not hurt the business. Security and availability are at odds with each other,” Favilla says. “If you want full security, no one is going to use anything. If you want full access to everything, you could be in serious danger. We have to acknowledge that.”
Comparison with 2017 Survey
While industry experts interviewed for this feature unanimously reported a perceived increase in the use of remote access technologies among their customers, a comparison with Automation World’s 2017 survey on this subject throws into question to what degree this increase has actually occurred. The 2021 remote access survey found that 67% of respondents are currently using some form of remote access technology; however, that number stood at 71.9% in 2017.
Of course, there are several possible explanations for the discrepancy. For one, it may be that respondents to the 2017 survey were using simple remote desktop software such as Teamviewer to issue commands to on-site human machine interfaces (HMIs) and industrial PCs (IPCs). By contrast, companies responding in 2021 are more likely to be harvesting machine data directly via the use of OPC UA and other similar methodologies.
Equally important is the way remote access technology applications have changed. When asked in 2017 what companies planned to use remote access for in the future, only 26.3% indicated that gathering manufacturing intelligence for use by plant management and corporate executives was on their radar. In 2021, that number had expanded to 49%, most likely reflecting ballooning interest in advanced analytics and enterprise-level optimization.
Moreover, growing cybersecurity concerns may have led some companies using remote access technology to scale back their use of it. In particular, the increasing prevalence of ransomware used to financially extort manufacturers has led many companies that previously would not have seen themselves as potential targets of cybersecurity attacks to reconsider whether or not the technology offers more benefits than liabilities.
Finally, the industry experts interviewed note that, although overall use of remote access technology was reported as being slightly higher in 2017 than in 2021, those who claim to have adopted the technology within the last year stood at 8% in 2021, as opposed to 3.8% in 2017. This implies that the perceived uptick in use amid the COVID-19 pandemic was not a mirage, as these results indicate that remote access growth in 2021 doubled in relation to 2017.
About the Author
David Miller
Former Senior Technical Writer

Leaders relevant to this article: