Cyber-attacks have been on the rise since the beginning of the pandemic, according to the Ransomware Task Force, an international coalition of experts formed to combat ransomware criminals. Ransomware is a type of malware used by attackers who threaten to publish the victim's data or block access to their systems unless a ransom is paid.
Ransomware targeting infrastructure and manufacturing is a profitable business for bad actors because the impact and money lost due to production downtime is reason enough for companies to pay up fast. And as manufacturers create more connections into equipment to keep operations running from afar, it creates new pathways for hackers to access.
“If you think about the history of controls, [these systems have] always been disconnected, so no one worried about security,” says John Livingston, CEO of cybersecurity firm Verve Industrial. He says companies installed firewalls to protect the network, but no one worried too much about security of the machines inside the network barrier. “So they didn’t patch them, they used standard passwords, and allowed more people access to an incredibly insecure infrastructure that was completely unmanaged,” he says.
Now, however, OEMs and industrial control system (ICS) suppliers are rapidly rolling out remote access tools as a way for plant managers to monitor machines from wherever they are. The problem is, there are way too many methods of remote access.
Cargill, a global manufacturer with facilities in 70 countries, is a good example of an industrial company working to secure their systems amid a rise in the use of remote access technology. “We have so many OEMs that we mostly deal with at the local level,” says Dominic de Kerf, Cargill’s smart manufacturing expert focused on automation, instrumentation, and process control. “They know a lot about their machines, but cybersecurity is not something they do well.”
And every supplier has a different remote access method, making the management of security systems to block access into an ICS opening an IT nightmare.
The concern was so great for de Kerf that, when asked to join a remote access workgroup within the Organization for Machine Automation and Control (OMAC), he gladly accepted. The OMAC workgroup is facilitated by ei3 Corporation, a provider of technology used to increase machine performance and secure remote connections.
Members of this group include large consumer packaged goods (CPG) manufacturers such as Cargill, Frito-Lay, and P&G, as well as OEMs like ITW Hartness, Durr USA, Milacron, Mettler Toledo, Nordson, and ProMach. Technology suppliers Beckhoff Automation, Mitsubishi Electric Europe, Sick, Siemens, and of course, ei3, as well as many system integrators and organizations like PMMI, the Association for Packaging and Processing Technologies, are also involved (note: PMMI is the parent company of Automation World).
The group has produced a 90-page Practical Guide for Remote Access to Plant Equipment which was released in January 2021. It details best practices to define, analyze, control, improve, and secure remote access. It walks readers through specific steps to safeguard a facility, focusing on processes and terminology—especially between IT and OT (operations technology) departments.
PMMI followed up with its own report, 2021 Cybersecurity: Assess Your Risk, which zeroes in on what OEMs need to pay specific attention to, noting that machine builders are highly vulnerable to cyber-attacks, as cyber-criminals see them as a bridge to reach other targets.
This focus on OEMs raises the question: Who is ultimately responsible when there is a security breach?
“At the end of the day, the manufacturer is ultimately responsible, but whoever is developing the platform is responsible for making sure it is deployed in a secure way,” says Jacob Chapman, a solutions architect with Nozomi Networks (formerly with Grantek at the time of this interview).
A universal approach
Manufacturers like Cargill are asking for vendor-agnostic tools dedicated to remote access security to avoid having to deal with a variety of proprietary offerings from different vendors.
This is a valid request “but it requires operators take control back from the OEMs,” Verve’s Livingston says. “And this is not just true with remote access, but [with cybersecurity tactics] across the board. We’ve given control over to people who make the control systems. Now manufacturers are beholden to the vendors. And as a CIO and chief security officer, you can’t say you are operating securely when there are 40 different vendors controlling your OT systems.”
Taking back control means managing the security of the production floor infrastructure. The Verve Security Center is an OT systems management platform for industrial control system cybersecurity, protecting the end points inside of OT. “It basically lets you do IT security in OT,” Livingston says. “You get the same functionality, but it is safe for industrial control systems.”
Verve partners with vendor-agnostic tools for securing the network, including Dispel.io and BeyondTrust.
For its part, the Dispel Moving Target Defense technology flips the model of the traditional static defense system. “Rather than having a static target, like a castle that adversaries are trying to hit, we build submarines that move and keep assets safe because they can’t see where they went,” says Ben Burke, chief operating officer at Dispel.
According to Burke, a traditional on-premises system may have several steps to connect through the firewall, but it is basically a beacon beckoning all to connect. “What’s different about the moving target defense is we push the connection entry point to the cloud and shift it over time, so you are not directly connecting to the OT environment. When you first connect, you have to go through our cloud infrastructure before getting there,” he says.
The on-premises gateway establishes an encrypted tunnel to the cloud network. Once that half of the bridge is built, the virtual desktop gets the user profile and connects to the other side of the network. The two come together to create a temporary bridge through which the user can access the encrypted tunnel through the gateway and firewall and then to the specific OT endpoint. This infrastructure cycles over time so that OT has a new virtual desktop with each log in. “For an adversary, every day the entire user profile has completely changed. There is no methodology for performing reconnaissance on it,” Burke says.
Systems integrator Grantek uses this Dispel technology in its Engineer-in-a-Box remote access tool, a plug-and-play appliance that provides secure remote access to an ICS. It just needs to connect to an Ethernet port anywhere on an OT network and to disconnect, just turn it off.
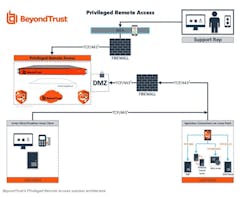
Separately, BeyondTrust is solving the security risks typical of Windows-based remote access products, as well as proprietary approaches associated with embedded systems. BeyondTrust’s Privileged Remote Access eliminates the use of risky open ports and closes remote access backdoors using the company’s Jumpoint technology, which serves as the remote desktop protocol broker.
The user logs into an appliance that sits either in the cloud or is installed on premises and deploys a piece of software that makes outbound connections into the appliance with multifactor authentication to all potential connection types.
“We set up all the connections and all you see is ‘machine 1, IoT 2, System 3,’ for example, and it opens it up for you,” says Morey Haber, chief security officer at BeyondTrust. “Jumpoint connects into the environment through an administrative screen where you can select where you want to go and choose the protocol needed to get there, whether it’s traditional Windows remote desktop protocol or Linux or embedded VNC. The same piece will broker any type of communications and allow work from anywhere into the critical infrastructure, including OT.”
It is secure because the end user knows nothing about devices downstream and they can’t do anything without signed permissions. In addition, passwords are changed each time, so even if a bad actor were to steal a password, it couldn’t be used.
The OEM element
OEMs hold a lot of responsibility when it comes to keeping equipment secure, but it’s not an area they tend to have a lot of expertise in. In response, several ICS and security vendors are delivering OEM-specific tools.
Rockwell Automation recently rolled out a tool that couples its FactoryTalk remote access cloud-based software—which allows OEMs to manage, configure, and initiate secure connections to customers’ equipment—with its Stratix 4300 remote access router installed at the customer’s site. The offering provides multifactor authentication and encrypted protocols. A digital input also gives onsite staff control of remote connections so that they’re only made when enabled locally.
“Together it creates a passive network that is outbound only,” explains Robert Ponsonby, Rockwell Automation’s global OEM partner program manager. Made more for monitoring than making changes on a machine, there’s no risk of someone getting in and messing with code, he says.
ei3 has its own OEM offering called the Amphion Edge Device. Using ei3’s virtual private network (VPN) appliance, it is a piece of hardware that acts as an edge device using industry standard security protocols to create a secure network from the machine to the ei3’s security application in the cloud, providing a managed secure network. “We are looking after the network, constantly patching and monitoring all aspects of a VPN,” explained ei3 founder Spencer Cramer, noting: “If you just put a VPN appliance on a machine and you are not updating it, that VPN appliance will quickly become a vulnerability to the organization.”
In addition to managing the security of the access point, ei3 controls the access of individuals. If an organization owns equipment from many different OEMs and uses services from different integrators or consultants, it’s not reasonable to open that equipment to everyone. “With the ei3 cloud security center, we give the owner of the equipment the ability to control the access to the equipment. They can create a temporary one-time link to open a door for a single person to access a single piece of equipment, and it’s all done through web pages, so no software or firewall configuration is needed. It’s done in a way that a plant manager or line supervisor can ask for support and, once it’s done, that door closes and locks.”
It’s also important to note that the ei3 technology works with any type of industrial automation controls and networks, including legacy protocols. “This is an important point because you can find hundreds of companies that will help you connect to brand new equipment, but [we can] help you with 15-year-old equipment,” Cramer says.
Verve’s Livingston agrees that understanding what’s already out in the field is an important part of foiling potential attacks. “OEMs are making investments in new devices, and all new code is being reviewed,” he said. “The problem is they have devices that have been in the field for years. How do they go back in time and review all that code that has been written over the last 30 to 40 years?”
That is where aDolus Technology comes in. The company, founded by Eric Byres, a recognized expert in ICS and IIoT cybersecurity, created the aDolus Framework for Analysis and Coordinated Trust (FACT). It is an AI-powered advanced aggregation, analytics, and correlation engine that creates up-to-date cybersecurity risk intelligence on software components as they flow between suppliers, developers, OEMs, service providers, and operators.
aDolus helps OEMs manage risk from incoming third-party software by automating compliance and governance. “It is a way to have a better understanding of the software supply chain, which provides a better ability to thwart a potential attack,” says Ron Brash, vice president of technical research and integrations at aDolus. “It provides OT asset owners assurance that files are tamper-free, authentic, and safe prior to installing on critical devices.”
Brash points to the SolarWinds hack as an example of how aDolus can help. “Many companies didn’t even know that they had SolarWinds products deployed in their OT systems because that software was supplied through an OEM. Thus, it took months for companies to address the issue even after it was publicly disclosed. Currently, asset owners, integrators, and many vendors do not have sufficient visibility into their product's vulnerability status, and asset owners are often unconsciously carrying that burden.”
Stay vigilant
While the industry has seen an increase in ransomware attacks since the beginning of the pandemic, Verve’s Livingston believes that it’s just the beginning. “I’d argue we’ve not yet seen the problems that will arise because of remote access issues.” He points out that a hacker typically sits in a system for 180 to 270 days before an attack happens. “If you do the math, we are about to get hit with bad times.” To stop—or at least manage a potential attack—means that you first need to get control over remote access, he says.
Leaders relevant to this article: