As any of our readers are certainly aware of, the accelerating acceptance of the Industrial Internet of Things (IIoT) brings with it security risks that need dealing with along the way. In fact, more than one-third of operational technology (OT) professionals in the enterprise identified security concerns as the largest impediment to production deployments of IoT projects, according to a study from 451 Research.
But how best to approach the security infrastructure needed for any given manufacturer or producer is no simple matter. Where best to put the time and money necessary to protect your assets?
The Industrial Internet Consortium (IIC), an organization focused on accelerating IIoT development, has been working on a Security Maturity Model (SMM) to help companies better understand how to progress toward their own security goals. It enables executives to focus investments on the security mechanisms that best meet their specific objectives. Along with the model itself, the organization has published a whitepaper—the IIC IoT Security Maturity Model: Description and Intended Use—that introduces the model, which is based on concepts identified in the IIC Industrial Internet Security Framework.
“The Internet of Things has brought a lot of innovation to industries, but it also introduces new security threats,” said Ron Zahavi, a co-author of the whitepaper. He serves as co-chair of the IIC Security Applicability group and is chief strategist for Azure IoT standards at Microsoft. “The security landscape is complex and always changing. It can be challenging for organizations to understand where to focus their security budgets, especially with limited resources. The Security Maturity Model provides organizations with an informed understanding of security practices and mechanisms applicable to their industry and scope of their IoT solution.”
There is a critical need for “a common, extensible model for IoT security to move the industry forward,” said Christian Renaud, IoT research director for 451 Research.
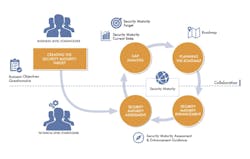
Organizations apply the SMM by following a process: First, business stakeholders define security goals and objectives, which are tied to risks. Technical teams within the organization or third-party assessment vendors then map the objectives into tangible security techniques and capabilities and identify an appropriate security maturity level.Organizations can then develop a security maturity target—including industry- and system-specific considerations—and capture the current security maturity state of the system.
“By periodically comparing target and current states, organizations can identify where they should make improvements,” said Sandy Carielli, whitepaper co-author and director of security technologies at Entrust Datacard. “Organizations achieve a mature system security state by making continued security assessments and improvements over time. They can repeat the cycle to maintain the appropriate security target as their threat landscape changes.”
Furthering explanation of the SMM, the IIC Security Maturity Model: Practitioners Guide will be released in the coming months and will contain the technical guidance for assessment and enhancement of security maturity level for appropriate practices.