Industrial control system (ICS) cybersecurity has been ramping up in a big way over the past few years and this year seems to be the breakout year for the release of a number of new cybersecurity products (see links at bottom of this article to access other recent Automation World coverage of new ICS cybersecurity products).
What’s intriguing about these new products is how they each have their own unique approach of providing security beyond the standardized IT approach of firewall use. Waterfall Security Solutions is no different in terms of having its own unique approach, but what's most interesting about them is how their system seems to have figured out a way to make the air gap between control systems and the outside world feasible.
Here’s what I mean: For years now, ICS cybersecurity professionals have gone to great lengths to explain how the “air gap” between the enterprise network and the ICS network does not really exist—regardless of how many engineers and technicians on the plant floor insist that it does. With so many networkable devices now in use, not to mention the use of laptops and mobile devices in manufacturing, the “air gap” separating the plant floor from the enterprise—and thus the rest of the world via the Internet—is not a viable approach to cybersecurity for modern industries.
Recognizing that the enterprise depends on a steady flow of manufacturing and/or operations data, Waterfall Security has developed a system that permits data to be collected and processed up to the enterprise networks without allowing data or commands to flow in the other direction.
As Lior Frenkel, CEO and co-founder of Waterfall Security, put it: “We enable data sharing without allowing access to the network. Our mission is to replace the misused firewall.”
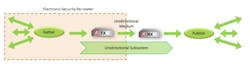
The core of Waterfall Security’s ICS cybersecurity approach is its Unidirectional Security Gateway, which combines hardware and software. “The hardware enforces security; no compromise of the gateway software can impair the security provided by the gateway’s hardware,” says Frenkel.
Unidirectional Gateway hardware includes a gather/TX module that contains only a fiber-optic transmitter connected to a publish/RX module that contains only a fiber-optic receiver. “The hardware can send information out of an ICS network, but is physically incapable of sending anything back into the ICS network,” says Frenkel. “This unidirectional feature of the Waterfall gateway cannot be changed, circumvented or hacked. As a result, security that the gateways provide from network-based attacks is, unlike firewalls, absolute.”
Once the data is out of the ICS, the gateway software replicates industrial servers to external networks. “Users and applications on external IT networks can access the replicas for data, or query them for processed information, and can be confident of receiving the same answers from the replicas as the original control system servers would have provided,” Frenkel says. “In this way, the Waterfall Unidirectional Gateway eliminates the need for access into control networks.”
“What is transferred between networks over the unidirectional medium is only the gathered data and enough meta-data to effectively describe the gathered data,” says Frenkel. “Each of the ‘gather’ and ‘publish’ applications are configured independently and manually as to what system and network addresses they communicate with on their respective networks. No addressing information whatsoever is communicated from the source/protected network to the destination/external network.”
Frenkel notes that Waterfall’s products have been deployed worldwide to protect everything from nuclear generators to refineries, offshore platforms and even geographically distributed systems, such as transmission substations and pipeline pumping stations. “Waterfall’s products are deployed because they reliably defeat network- based cyber-sabotage attacks, even the professional-grade, targeted attacks that routinely defeat firewalls and other software-based security protections,” he says.
He adds that more than 90 percent of Israel’s critical infrastructure is protected with Waterfall’s products.
Underscoring Waterfall’s success with its approach is the recent partnership agreement between Schneider Electric and Waterfall to bring Waterfall’s security products to Schneider Electric customers.
According to the Schneider Electric release announcing the partnership, Waterfall’s security approach “simplifies compliance with industrial cybersecurity standards and best-practices, ranging from the power sector’s NERC CIP standards to the cross-industry IEC 62443 and NIST documents.”
Recent Automation World coverage of new ICS cybersecurity products:
Leaders relevant to this article: