For years now, the prevailing attitude among many manufacturers has been that cybersecurity was among their least important concerns. Outside of critical infrastructure, most manufacturers thought the odds of their systems being hacked by outsiders was about the same as them winning the lottery. And though the odds of cyber hacking remain low for most manufacturing organizations, those odds appear to be increasing by the day.
The increase in odds I’m referring to is a result of a growing number of incidents like the WannaCry ransomware attack that affected production at automotive manufacturers Nissan, Honda and Renault as well as PetroChina. Then there was the NotPetya malware that, though targeted at Ukrainian and Russian power, transportation and communication operations, also affected Merck and Mondelez International in the U.S.
More recently there was the WikiLeaks revelation about a malware known as Brutal Kangaroo. The WikiLeaks information claims Brutal Kangaroo was developed by the CIA to specifically target air-gapped networks. The site Security Affairs reports that “Brutal Kangaroo is a tool suite for Microsoft Windows that targets closed networks by air-gap jumping using thumb drives. Brutal Kangaroo components create a custom covert network within the target closed network and providing functionality for executing surveys, directory listings and arbitrary executables.”
It might still be tempting for most manufacturers to think they are largely immune to infiltration by such malware. However, the history of these incidents show that these things have a way of spreading beyond their initial, intended targets.
With this in mind, I spoke with Dana Tamir, vice president of market strategy for Indegy, an industrial cybersecurity company. I asked her if manufacturers and processors, in general, should be concerned about Brutal Kangaroo.
“Most manufacturers already understand that air gapping is not a valid security strategy; disconnecting ICS from the external world doesn't guarantee that cyber threats won't find their way in,” she said. “For those who still believe in air gapping their ICS, this is a wake-up call.”
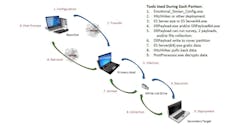
In some reports on Brutal Kangaroo, there was information that noted the malware could infect Internet-connected machines without having to first be installed via a thumb drive (the initial method of propagation for Brutal Kangaroo—as shown in the image accompanying this article). Tamir does not know for sure how this could happen since Indegy has not yet fully researched the capabilities of this tool. However, she said one way this could happen would be through a multi-stage infection process.
“For example, a USB drive is often used to transfer files in and out of the environment,” Tamir said. “If such a USB was connected to an Internet-facing machine which was compromised, the USB can become infected and used to transfer the threat into the environment.”
As a manufacturer, whether you see yourself as a potential hacking target or not, the increase in malware and related industry breaches underscores the fact that it’s time to start getting serious about your cybersecurity measures.
I asked Tamir what manufacturers can do to protect themselves from Brutal Kangaroo or similar hacking tools that can enter their networks either via Internet-connected machines or thumb drive infection. “Visibility is key to security,” she said. “Manufacturers must have the ability to monitor ICS activity and get early alerts that enable them to quickly respond and mitigate threats like this before it's too late.”
Leaders relevant to this article: