Though there are still a number of holdouts throughout industry, it’s increasingly becoming accepted that an air-gap approach to industrial control system (ICS) cybersecurity is no longer practical. This realization is occurring for several reasons, including the difficulty—if not impossibility—of maintaining a completely air-gapped ICS. Plus, an air-gap approach to cybersecurity puts companies at a competitive disadvantage when it comes to taking advantage of Internet of Things (IoT) capabilities such as remote monitoring.
Larry O’Connell of Microsemi, a provider of semiconductor and related systems to industrial companies, contends that air gapping can also “make the network less secure because it is harder to manage and issues are harder to diagnose. In addition, isolated networks are more difficult to scale, reconfigure or extend as companies adopt new technologies, update supply chains or adapt to new competitive opportunities and threats.”
Few IT managers would consider “permanently disconnecting their internal networks from the Internet for the sake of security,” says Roger Hill of Veracity Security Intelligence, an ICS cybersecurity platform provider. “Neither would they rely solely on firewalls for security under the assumption that firewalls are perfect malware filters or that employees, contractors or visitors won’t introduce a piece of malware by plugging in a laptop, inserting a USB drive, or clicking an email link. They have to assume that malware will get on their internal networks and will try to do harm.”
Note: Microsemi collaborates with Veracity to develop secure networking solutions for industrial Ethernet deployments.
To address these cybersecurity issues, Hill says IT uses what is known as centralized security orchestration to protect its networks. And as industrial companies increasingly integrate IoT capabilities to expand their businesses, it’s becoming apparent that operations technology (OT) infrastructure managers now require the centralized security orchestration that their IT counterparts have long used.
Hill says centralized security orchestration features five key capabilities:
- Networkwide situational visibility. This capability identifies what nodes (devices and ports) are talking to what other nodes, what protocols are in use, what devices are present on the network, traffic volumes between nodes, etc.
- Anomaly identification. This feature shows how the current situation differs from historical norms or from what’s expected (for instance, traffic spikes on a port talking to the Internet during non-working hours).
- Management by policy. This involves setting alerts or taking other actions automatically when pre-defined anomalies occur.
- Centralized programmatic control. This process addresses the reaction to alerts as well as proactive steps such as isolating subnets from the rest of the network (or the Internet), disconnecting a device, or shutting down a subnet as a last resort.
- Single pane of glass. This term refers to the ability of network operators to do all the tasks listed above without having to switch between interfaces, learning device-specific commands, or reading equipment vendors’ technical manuals.
Hill says that these five capabilities “affirm an important principal fundamental to both OT and IT—that network management and network security are inseparable. The ability to spot anomalous traffic volumes or change subnet partitioning, for example, speaks to both operational performance and security.”
Highlighting the system features OT needs to protect its networks like IT professionals protect their networks does not, however, address the unique challenges that OT network managers face.
According to O’Connell, some of the unique challenges faced by OT but not typically encountered by IT, include:
- Proprietary barriers. “Industrial networks are rife with solutions that speak to different protocols and obey different command syntax that are tightly bound to their controllers, which in turn are tightly bound to particular supervisory software,” O’Connell says. “That’s why mixing and matching solutions at different levels of the control hierarchy is very difficult, and why what should otherwise be a simple PLC switch-out, for example, often requires replacing an entire skid, resulting in expensive downtime, lost production and lost revenue. Increasingly, equipment vendors are addressing this issue with software-programmable ‘white label’ devices, particularly switches, which allow for on-the-fly swap outs and topology changes under remote—and potentially centralized—software control.”
- Limited security controls. Legacy operations environments defined by proprietary islands of technologies leave network operators with few options when it comes to implementing security policies. In such environments, there is no centralized configuration capability, little to no auditing of configurations and limited security controls at the switch itself. “If you want to inspect or change port settings, you have to physically visit a switch,” O’Connell says. “This often leads to inefficient performance or simply wrong network configurations. On a security basis, this also means operators cannot see patterns of activity across the network that could pose potential threats. As a result, they are unable to respond to those threats swiftly and with minimal disruption.”
In addition to these realities, OT network managers can’t simply shut down part of their network when threats occur. Therefore, “security orchestration must be even more aligned to their requirements than one might typically find in IT,” says O’Connell.
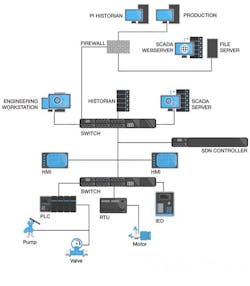
The answer, according to Hill, is to split the control layer from the data layer.
Hill explains that, to do so, a software defined network (SDN) controller manages the network centrally and makes decisions on how the network should handle the data. The SDN controller communicates with the network infrastructure using open application program interfaces (APIs) supported by SDN-enabled elements (like Ethernet switches). “Using this architecture, we can have better visibility of the network and are able to more easily optimize the design for security,” he says.
By separating the control and data layers in this manner, you can “define security zones, event thresholds and other control features in software rather than in hardware, allowing OT to achieve the same flexible, policy-driven distributed network management as IT while overcoming OT's inherent security and management challenges,” says Hill. “The only other requirement is to also implement security information and event management software that is capable of leveraging hardware vendors, like Microsemi, committed to this type of seamless environment.”