Coming from Seattle, David Mattes likes to talk about what happens when an “unstoppable force” (the Denver Broncos offense) meets an “immovable object” (the Seattle Seahawks defense). In the case of Super Bowl XLVIII, the result was a win for the Seahawks. The case of industrial networks has a somewhat different result.
With the Internet of Things we hear so much about (some 75 billion devices could be connected to the Internet by 2020), connectivity becomes that unstoppable force. The immovable object is industry’s legacy systems, Mattes says. “When these things collide, great things can come out of it, and great challenges and problems as well.”
Mattes is founder and CEO of Asguard Networks, a company that grew out of work at The Boeing Company, where Mattes was asked to tackle network security. The challenge he discussed last week at The Automation Conference 2014 in Chicago was connecting the Boeing 777 manufacturing line through the enterprise-wide network.
The lean manufacturing operations at Boeing had a “tremendous number” of sensors, HMIs, motor drives, etc., that needed to be able to connect to the enterprise network, Mattes said. “But there was no good way to connect this equipment to the enterprise network. Rather than approach IT, they approached my [R&D] group,” he said. “To solve a general class of problems, I wanted to give the automation group their own sandbox, but also satisfy corporate for being a good network citizen.”
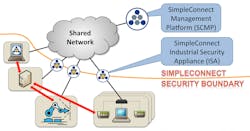
The network that Mattes and his team developed and later commercialized through Asguard is based on the ISA 100.15.01 architecture (see chart), leveraging a shared network infrastructure but isolating integrated control system (ICS) devices from the network. They wanted to minimize the attack surface by limiting connectivity to the absolute minimum.
To do that, they created a model of split responsibility between engineers and IT. “They need to be agnostic to underlying connectivity,” Mattes said, explaining that the operations group is able to retain networking configuration control. “Automation has made tremendous strides with IT, but IT has not made advances when it comes to managing security within manufacturing.”
There are several benefits to this kind of split architecture throughout the organization, Mattes said. For operations, retaining network configuration control means that no configuration changes are required, they can modify configuration on their own terms, there’s centralized lifecycle management of private networks, and the segmented networks are easier to operate and maintain.
The architecture also enables IT to provide secure private networking as an internal service, delegating control to operations users and groups. Organizationally, it provides a clear line of responsibility, reduces total cost of ownership (TCO) compared with other solutions, reduces the network attack surface, and provides more robust control system networks.
Asguard’s SimpleConnect network architecture was built on the idea that there must be a better way than traditional solutions—something that would have some of the flexilibity of a direct connection but with more security. Even VLANs and firewalls are not ideal in terms of security, Mattes explained. “VLAN is really just another perimeter security model,” he said. “This actually becomes a very expensive network to maintain over time.” A firewall is a “great first step, but it does not provide any integrity protection of the data,” Mattes added. “You have to be sure that the data you’re getting is what you think it is. Also, it’s hard to dynamically adjust policies to allow remote access.”
SimpleConnect connects to a shared network using any kind of connection option that’s available—even enabling operations to leverage cellular networks. The ISAs only communicate with each other using secure protocols. “There’s no visibility across the security boundary, but devices have the impression that they’re talking directly to each other,” Mattes explained.
With this constrained connectivity model, even if an attacker were able to penetrate the network, they would have a much smaller ability to propagate that attack to any of the other assets on the system.
After developing this network architecture for Boeing, Mattes led the move to commercialize the solution through the launch of Asguard Networks. “I really wanted this to be something that could solve industry problems in general, and could be an industry solution,” Mattes said.