A Security Framework for the Industrial Internet
A mainstay of discussions surrounding industrial control system cybersecurity is that the process of securing such systems should not be addressed in isolation. In other words, cybersecurity should not be approached on a piecemeal, device-by-device basis.
Though leading industrial cybersecurity recommendations tend to suggest similar best practices, their origin from a variety of sources—often with products of their own to sell—can sometimes be skewed toward approaches that emphasize the use of certain products, or at least certain types of products. As a result, there has been a distinct need for an independent industrial cybersecurity standard that addresses specific Industrial Internet of Things (IIoT) requirements.
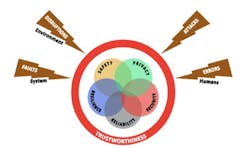
With the publication of the Industrial Internet Security Framework (IISF) by the Industrial Internet Consortium (IIC), industry now has a common security framework that addresses security issues in IIoT systems. The IISF, which is available free of charge at www.iiconsortium.org/IISF.htm, emphasizes the importance of five IIoT characteristics—safety, reliability, resilience, security and privacy. The framework also defines risk, assessments, threats, metrics and performance indicators. Additionally, the IISF separates security evaluation into endpoint, communications, monitoring and configuration building blocks with subdivisions for each one. Each perspective offers implementation best practices.
The IISF also takes an extra step—going beyond technology characteristics, threats and metrics—to separate the industrial space into three roles to help clarify distinct layers of responsibility as they apply to IIoT cybersecurity. The three roles identified in the IISF are component builders, system builders, and operational users. According to the IISF, component builders create hardware and software; system builders combine hardware and software solutions to create systems; and operational users are the owner/operators of the systems who manage the risk to their industrial processes posed by the systems. To ensure end-to-end security, industrial users must assess the level of trustworthiness of the complete system and each component and role in it.
“To add security to an industrial system, you must make sure it won’t interfere with safety and reliability requirements,” says Dr. Richard Soley, executive director of the IIC. “The IISF explores solutions to industrial problems that have plagued the industry for years. The IIC is also putting the IISF vision into practice in our testbed program.”
Speaking of IIC testbeds, the IIC has just approved an IIC testbed for legacy sensor-to-cloud connectivity called the Smart Manufacturing Connectivity for Brownfield Sensors Testbed. Unlike new deployments, where IIoT levels of connectivity can be designed into sensors from the beginning, brownfield installations require processes and tools that will enable easy integration at both the operations technology (OT) and the IT level.
Led by IIC member TE Connectivity (TE), testbed participants also include SAP, ifm, and the OPC Foundation. Goals of this testbed include:
- Introducing a retrofit hardware solution (the "Y-Gateway") that makes use of existing physical connectivity;
- Extracting sensor data from the automation system without impacting operations;
- Delivering the sensor data to SAP’s platform through a secure OT/IT communication based on OPC UA (IEC 62541); and
- Defining and implementing a common device model based on an available open standard to allow for the integration of an IO-Link sensor with IT, enabling the remote configuration of the sensor.